Last week, Google announced that Gmail users can email their Google+ connections without knowing their email address first. For some, it’s an easy way to stay in touch. For others, it’s a ticket to unwanted email. However you feel, here’s how to turn the feature off, or set it so only the people you want can use it.
Now that the new feature has rolled out to Gmail users (although it hasn’t gotten to Google Apps users, as far as we can see), controlling who can email you is pretty simple:
- Click here to open the General tab in your Gmail Settings.
- Scroll down to Email via Google+.
- Click the drop-down and select your preferred option. “Circles” (which was the default for me) only allows people in your circles—not those who have circled you—to contact you. “Extended circles” allows friends of your friends to email you. “Anyone on Google+” is as the name implies, and we’d suggest avoiding it. To turn the feature off completely, select “No one.”
- Scroll down and click “Save Changes.”
That’s it.
MarkMonitor Inc, USA based company who is responsible for over 110 domains including google.com.pk, microsoft.com.pk, paypal.pk, domain control panel hacked, last night and some sites are still down as of (24th November, 2012)
Google Pakistan’s home page (google.com.pk) is “hacked” by Turkish hackers putting a message which says “Pakistan Downed”. Paypal site is still down and showing this:-
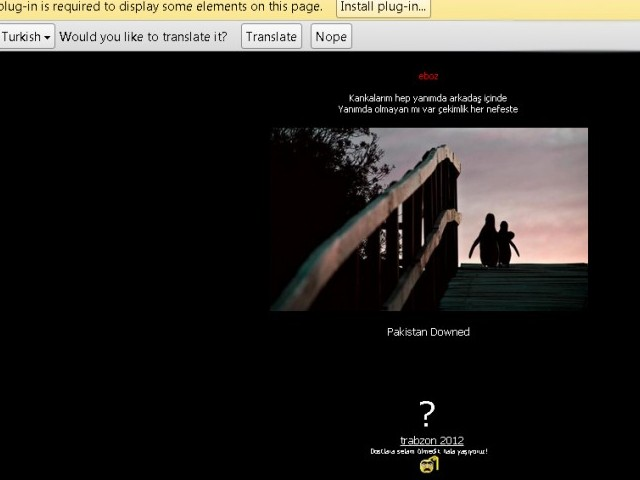
WHOIS record of those hostings point to some free hosting service as DNS providers:-
dns1.freehostia.com
dns2.freehostia.com
List of sites affected:-
A subset mirror of the Google Libraries API CDN meant to be served from your local development machine when internet access is lacking. This will increase your overall browsing experience. (for sites like wordpress, Blogspot, Google products etc)

Read the rest of this entry »
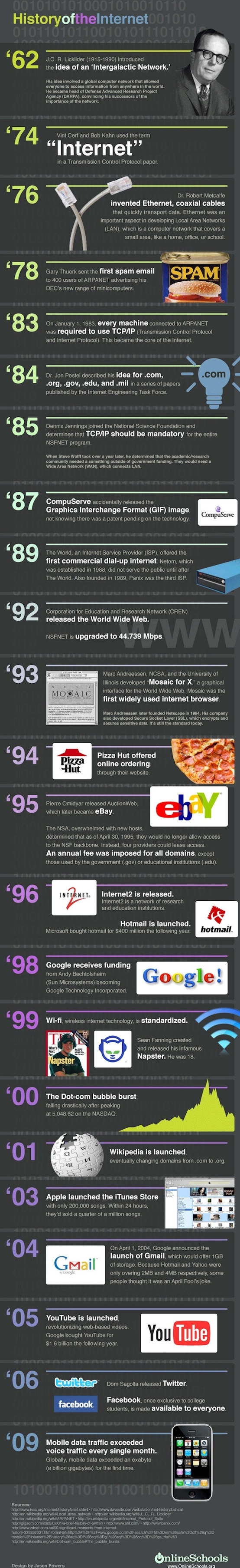
Yet another infographic. Well, Infographics are much better way to grasp the information, especially if they’re well made. This cool infographic from OnlineSchool lists out some of the most important events in the history of the internet.
Comodo is one of the largest SSL and Code Signing Certificate provider, some Comodo certificates were hacked earlier this year and now ComodoHacker claimed hacking DigiNotar a Dutch Code Signing/SSL provider company.
Meanwhile, the fallout from the hack continues. DigiNotar has, in effect, lost its status as a trusted root certificate authority. Its certificates have been blacklisted by Microsoft, Google, Mozilla, and Apple.
With this hack the hacker can intercept all encrypted communications of Windows Update and other microsoft services, Gmail , Mozilla based and Apple services without user knowledge.
Also Microsoft and Firefox just released a security update to block all DigiNotar based certificates. (Kindly update your systems now)
ComodoHacker also justifed his attack on the Dutch certificate authority by blaming the Dutch for the murder of 8,000 muslims at Serbian hands in Srebrenica; "It's enough for Dutch government for now, to understand that 1 Muslim soldier worth 10000 Dutch government."
Here is the Interview of the Iranian Hacker who was behind Comodo and DigiNotar hacking.
Hi
I have received around 25 interview requests, I'll give response to all requests, I'll give interviews to all.
Just to make some points which I see around in internet about me and in some interview questions:
a) I'm single person, do not AGAIN try to make an ARMY out of me in Iran. If someone in Iran used certs I have generated, I'm not one who should explain.
b) This attack was really more sophisticated than simple Stuxnet worm. 0-days? I already have discovered similar bugs, trojan? I already wrote most sophisticated undetectable ring0 and ring3 rootkit (works together), signing certificates? huh, man! I have around 300 code signing certificates and a lot of SSL certs with again code signing permission, look at Google's cert, I have code signing privilege! You see? I owned an entire computer network of DigiNotar with 5-6 layer inside which have no ANY connection to internet, I have so much to explain, but later… You have to wait!
c) I still have access to 4 more CAs, I just named one and I re-name it: GlobalSign, StartCom was lucky enough, I already connected to their HSM, got access to their HSM, sent my request, but lucky Eddy (CEO) was sitting behind HSM and was doing manual verification.
d) I'm able to issue windows update, Microsoft's statement about Windows Update and that I can't issue such update is totally false! I already reversed ENTIRE windows update protocol, how it reads XMLs via SSL which includes URL, KB no, SHA-1 hash of file for each update, how it verifies that downloaded file is signed using WinVerifyTrust API, and… Simply I can issue updates via windows update! You see? I'm so smart, sharp, dangerous, powerful, etc. huh?
I'll talk about more stuff later. May I also start a web hacking course for Anonymous and Lulzsec and friends of them, Rootkit development for Stuxnet developers, 0-day vuln. assessment in Windows and Linux environment for Stuxnet developers and other hackers too. huh? What do you think?
Dutch government is paying what they did 16 years ago about Srebrenica, you don't have any more e-Government huh? You turned to age of papers and photocopy machines and hand signatures and seals? Oh, sorry! But have you ever thought about Srebrenica? 8000 for 30? Unforgivable… Never!
I heard also that Dutch government tries to gather documents and make a compliment against Iran, really? Shame on you man! Have you been in court for Srebrenica? Who should file compliment for Srebrenica? You should pay, these are consequences of Srebrenica, just know it! This is consequence of fighting with Islam and Muslims in your parliament.
WOOOOORLLLLDDD! Wait for me, you have so much more SHOCKINGS to see from me! From a person who came to this world just 21 years ago! JUST WAIT!