The Linux Auditing System and auditd are a great way to monitor who and when changes are made to the files in your website. To install and configure follow these steps:
1. Install auditd and related utilities:
yum install audit
2. Make sure auditd is running:
/sbin/chkconfig --list auditd
auditd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
3. Edit /etc/audit/auditd.conf and change:
action_mail_acct = [your email address]
This sets any action emails to go to your preferred address.
4. Edit /etc/audit/audit.rules and add a line like this to the bottom:
-w [path_to_website] -p wa -k [key]
So if you website is located at:
/var/www/vhosts/mysite.com/httpdocs
Then a command like:
-w /var/www/vhosts/mysite.com/httpdocs -p wa -k mysite
would setup auditing of write and attribute change requests. Events matching this rule would be tagged with the “mysite” key.
/sbin/service auditd restart
Audit logs go to:
/var/log/audit/audit.log

“Don’t tell anyone that I’m free”
WinSSH
Update (10/July/2016): OpenSSH (7.2p2) Server for Windows (7.2p2 is latest version of OpenSSH)
OpenSSH (6.4p1) Server for Windows (Previous version of OpenSSH)
General Features:-
* Security, if you want to access your Windows Machines cmd shell with full security.
* Windows NT Service Support
* Full install about 12mb, installer under 8mb (Including Cygwin dependencies)
* Windows Command Prompt support for SSH Terminal
* SCP/SFTP server support (secure file transfer)
* Command-line clients included Read the rest of this entry »
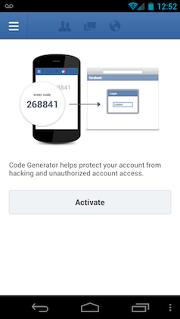
What is Facebook’s Two-Factor Authentication?
Facebook’s two-factor authentication (a.k.a Login Approvals) is an added security feature used to help prevent hackers from logging into your account with a stolen password. It helps you prove to Facebook that you are who you say you are. This is done by Facebook determining that you are connecting from a previously unknown device or browser and issuing you an authentication challenge, requiring you to enter a numeric code that generated by using the Code Generator tool from within your smartphone’s Facebook app.
Once you have entered the code you received on your phone, Facebook will allow the login to take place. Hackers (whom hopefully don’t have your smartphone) will not be able to authenticate since they won’t have access to the code (unless they have your phone)
Read the rest of this entry »
There is a worldwide, highly-distributed WordPress attack that is ongoing on most of the WordPress powered blogs.
The following steps can be used to secure (by password protection) wp-login.php for all WordPress sites in your cPanel account:
How to Password Protect the wp-login.php File
There are two (2) steps in accomplishing this. First you need to define a password in the .wpadmin file, and then you activate the security in the .htaccess file. Read the rest of this entry »
Attack from just 49 IPs and 48,000 servers (Linux/HP Unix) boot records were deleted in South Korea (20-March-2013), including servers at major (4) Banks and (3) TV stations.
Read the rest of this entry »