You might heard about Application‐level DDoS (Distributed Denial of Service) attacks on websites such as Twitter, Facebook and Wikileaks. Usually those kind of attacks involves a large number for HTTP/HTTPS requests to specific part of the website that could potentially eat up all the resource of the server resulting unresponsive behavior from the web server.
There are already some tools available to shut down any website and make it unreachable for legitimate users.
Looking at the technique used to perform this attack, the tool sends about 10 Long HTTP/HTTPS requests per second until it reaches bandwidth or connection limits of the hosts or networking equipment to make it offline.
Now the question is how we can stop this attack? What are the preventive measures against the Layer7 DDoS?
First of all, we start limiting the traffic using hashlimit on iptables. This module can be used to allow just a certain number of packets per minute:
iptables -A INPUT -p tcp --dport 80 -m hashlimit --hashlimit-upto 50/min --hashlimit-burst 20 --hashlimit-mode srcip --hashlimit-name http -j ACCEPT
iptables -A INPUT -p tcp --dport 80 -j DROP
where "–hashlimit-burst 20" is the burst limit, you can adjust as per your requirement.
Also using Apache you can add a module mod_reqtimeout. This directive can set various timeouts for receiving the request headers and the request body from the client.
Hope this helps…
CMOS De-Animator is a service utility for your system’s CMOS RAM. Unlike its predecessors, this new version includes a graphical interface and CMOS-backup options along with the “Clear CMOS” procedure, which was the original version’s only purpose. So, you can now backup the main CMOS settings to a file, or restore them later. The application supports all 32-bit and 64-bit Windows operating systems except Windows 95 and Windows NT 3.51; for these old systems, you have to use De-Animator’s previous version. You could possibly use it to reset BIOS Password from Windows itself!
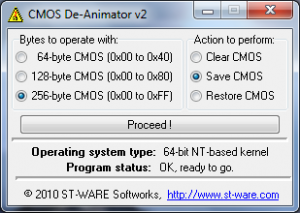
CMOS De-Animator
CMOS De-Animator is not a tool for regular users but for system administrators or hardware engineers who find users who have forgot their CMOS password. For them, this tool is really helpful. Use it with care if you are a novice user
Downlaod CMOS De-Animator v2.0 here
Network security is a completely changing area; new devices like IDS (Intrusion
Detection systems), IPS (Intrusion Prevention systems), and Honeypots are modifying the
way people think about security. Companies are spending thousand of dollars on new
security devices, but forgetting the basic, the first line of defense: the border router.
Although a lot of people may think that routers don’t need to be protect, they are
completely wrong. A lot of secure problems appear all time against this kind of device
and most of them are vulnerable. Read the rest of this entry »